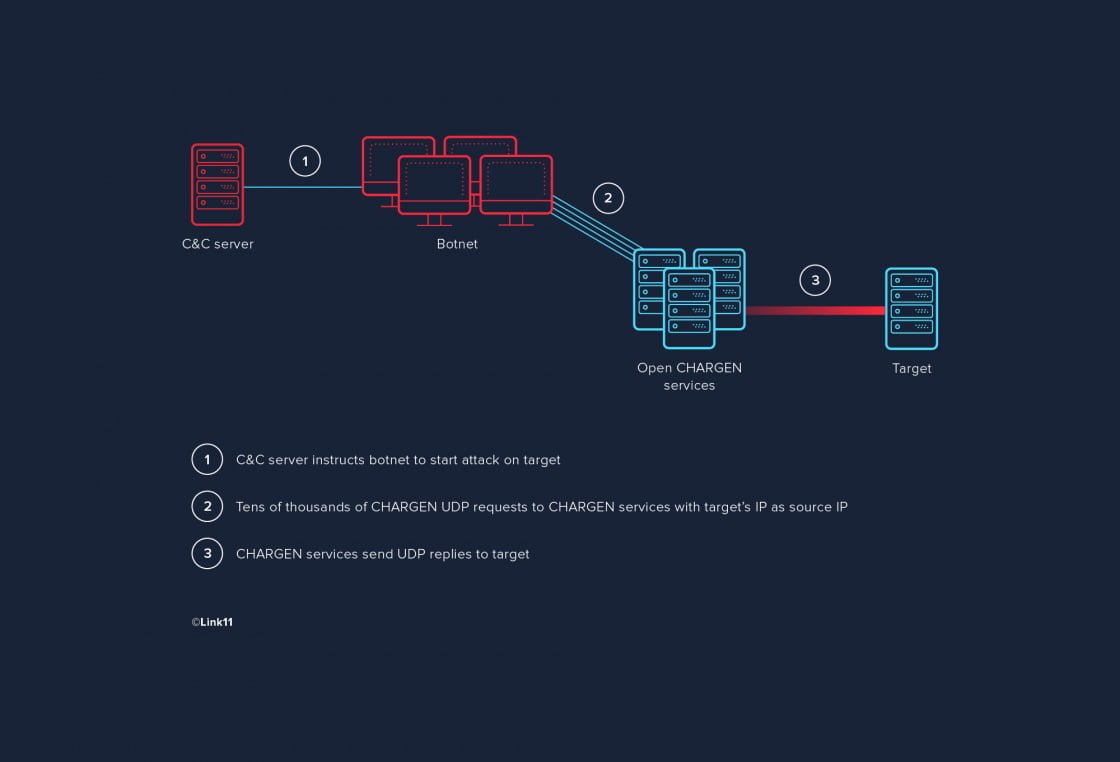
Charging Port Board For Motorola Moto E6 Play Xt2029 Xt2029-1 Charging Port Board Cellphone Replacement Parts Usb Charger Board - Mobile Phone Flex Cables - AliExpress

10pcs For Sony Srs-xb13 Type C Usb Charger Jack Connector Charging Port Socket Plug - Mobile Phone Flex Cables - AliExpress

USB Charging Port For LG Nexus 5 D820 D821 Durable Charging USB Port Dock Connector Mic Flex Cable|Mobile Phone Flex Cables| - AliExpress