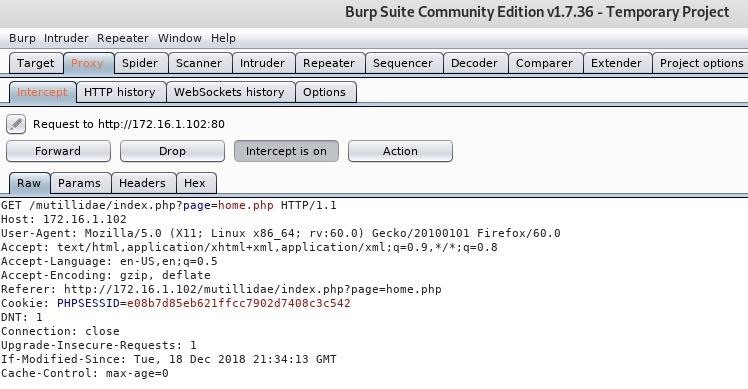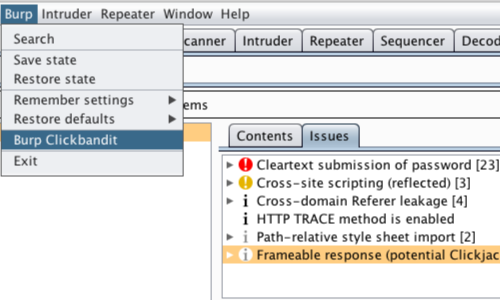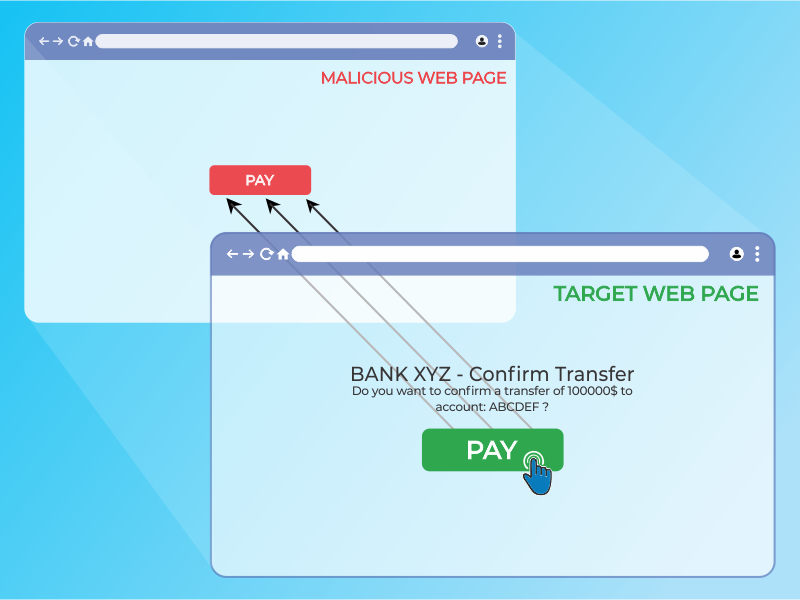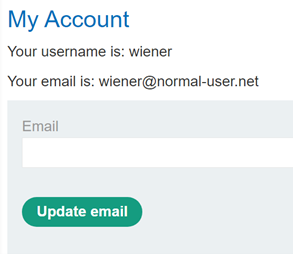
How to Generate a Clickjacking Attack with Burp Suite to Steal User Clicks « Null Byte :: WonderHowTo
How to Generate a Clickjacking Attack with Burp Suite to Steal User Clicks « Null Byte :: WonderHowTo
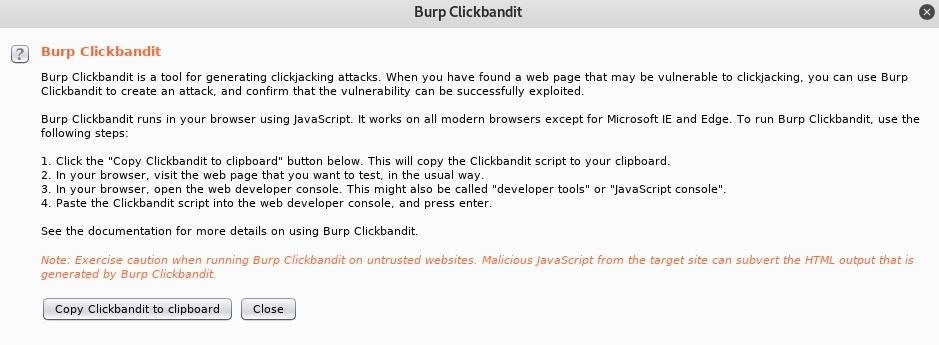
How to Generate a Clickjacking Attack with Burp Suite to Steal User Clicks « Null Byte :: WonderHowTo
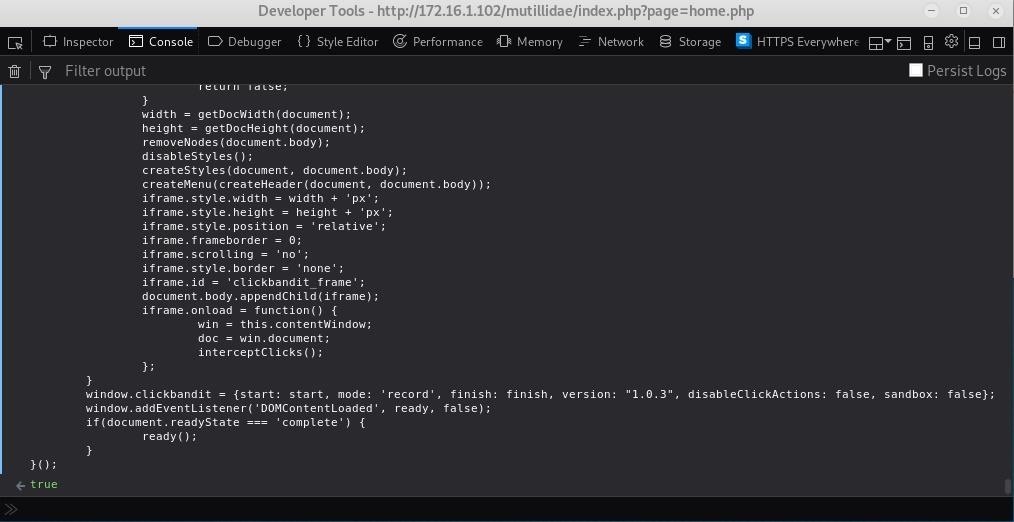
How to Generate a Clickjacking Attack with Burp Suite to Steal User Clicks « Null Byte :: WonderHowTo
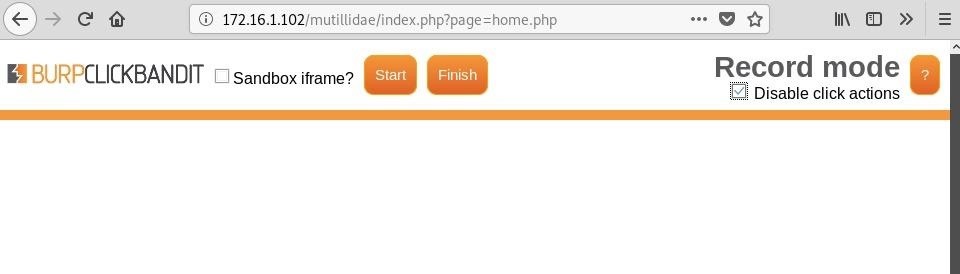
How to Generate a Clickjacking Attack with Burp Suite to Steal User Clicks « Null Byte :: WonderHowTo
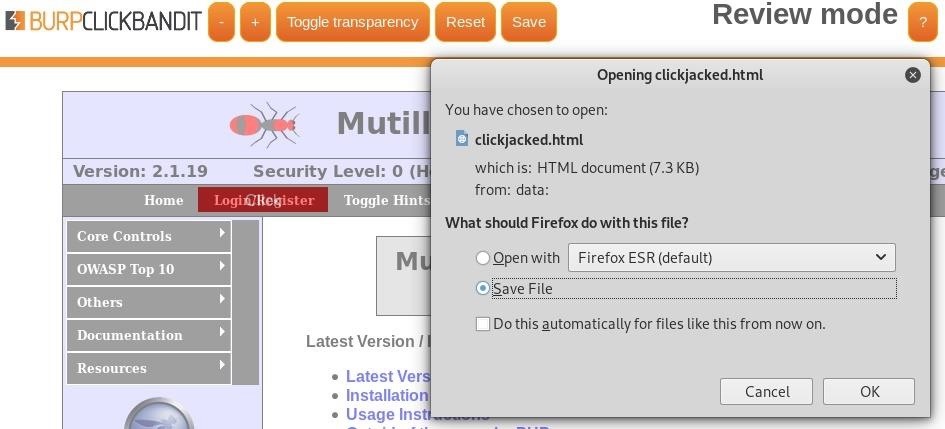
How to Generate a Clickjacking Attack with Burp Suite to Steal User Clicks « Null Byte :: WonderHowTo