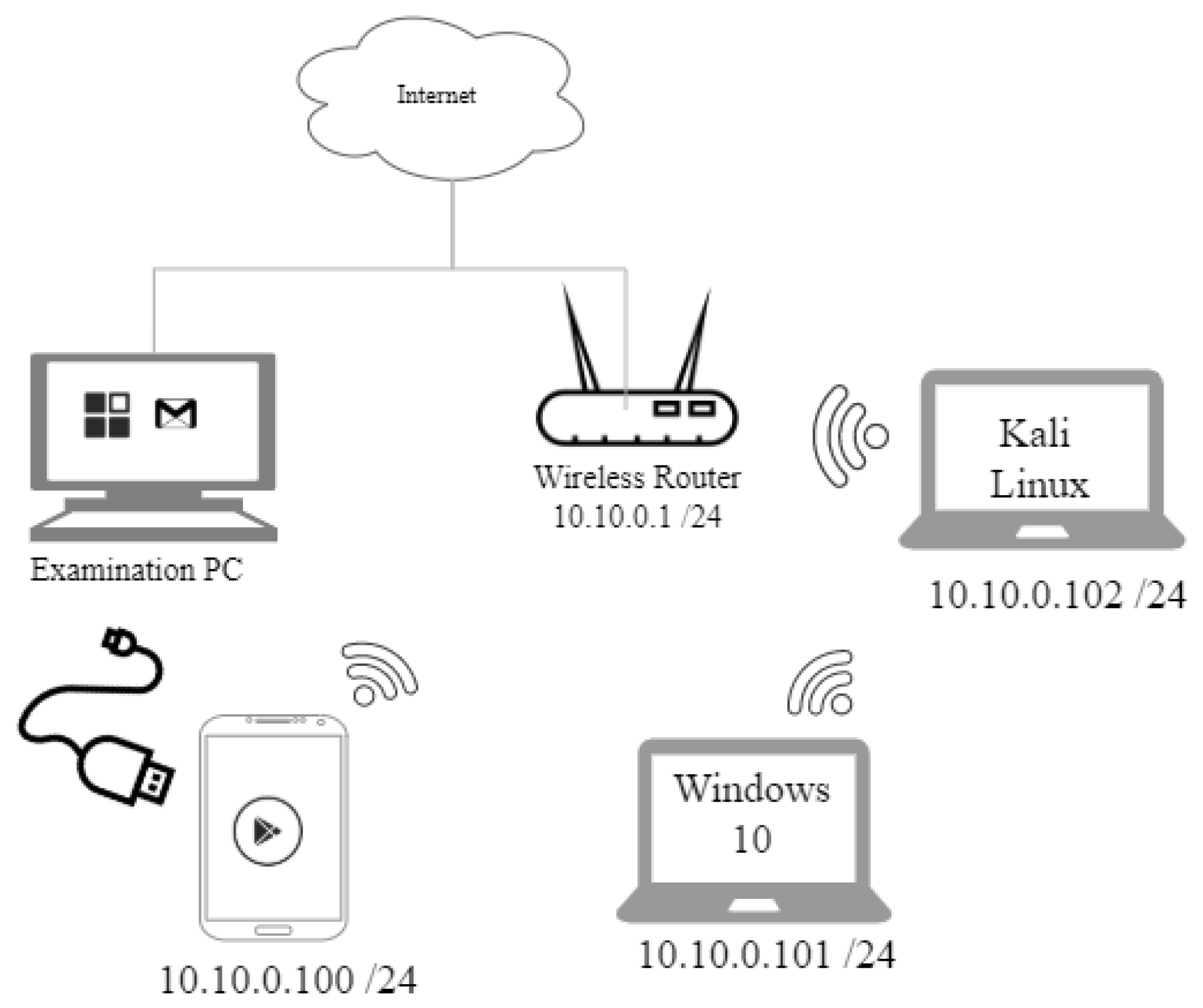
Amazon.com: Panda Wireless PAU06 300Mbps Wireless N USB Adapter - w/ High Gain Antenna - Win XP/Vista/7/8/10/11, Mint, Ubuntu, MX Linux, Manjaro, Fedora, Centos, Kali Linux and Raspbian : Electronics

Linux Basics for Hackers: Getting Started with Networking, Scripting, and Security in Kali: OccupyTheWeb: 9781593278557: Amazon.com: Books

Multiple vulnerabilities found in Wireless IP Camera (P2P) WIFICAM cameras and vulnerabilities in custom http server - IT Security Research by Pierre



![How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/9-23.png)


![How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/5-74.png)