How to deal with Value Unconverted in SAP Tables for CDS Views, Calculation Views or BW Enhancement | SAP Blogs

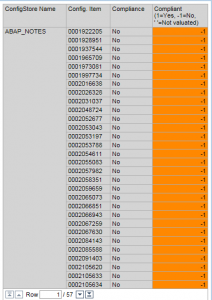
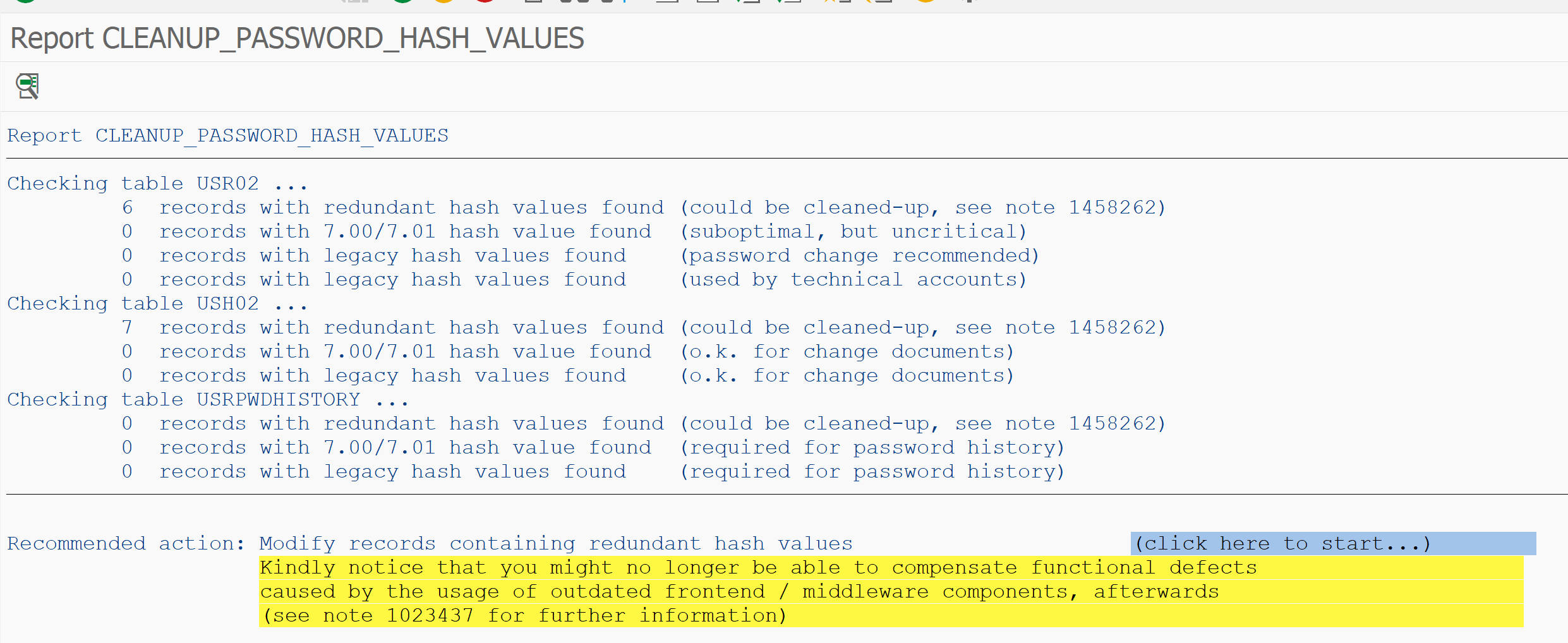
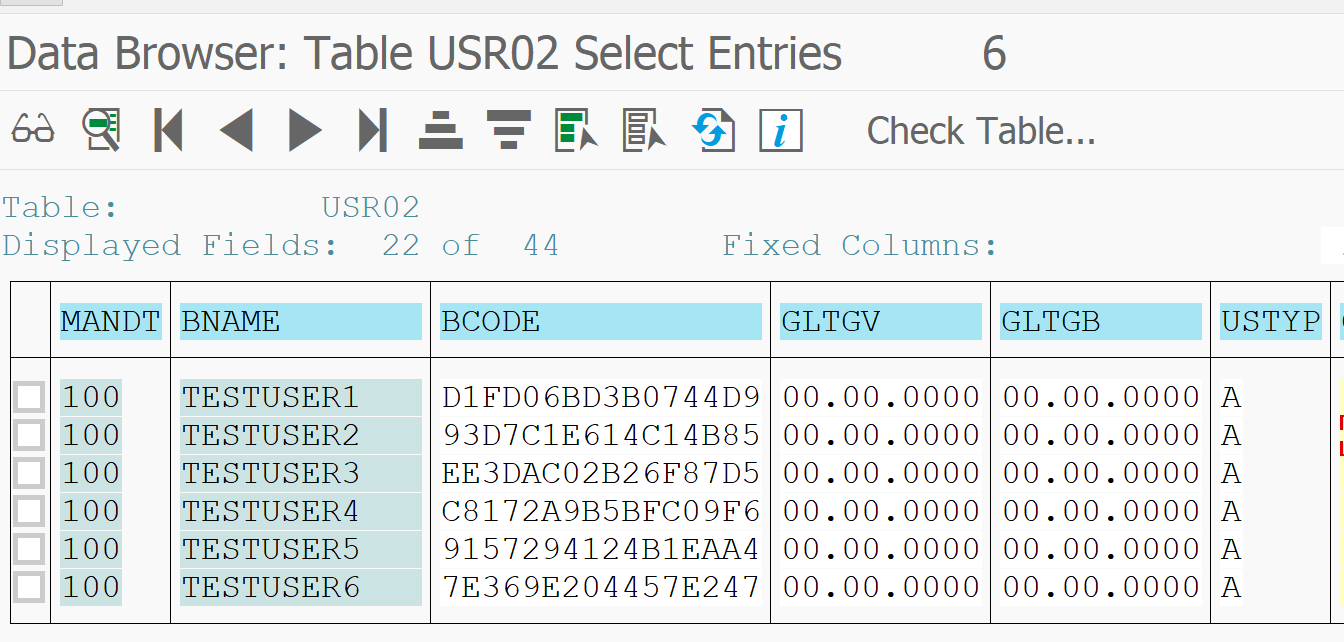
CUA Log – Password hash is rejected; password is deactivated. Securing ABAP systems via iterated salted hash iSSHA-1. | SAP Blogs

CUA Log – Password hash is rejected; password is deactivated. Securing ABAP systems via iterated salted hash iSSHA-1. | SAP Blogs

CUA Log – Password hash is rejected; password is deactivated. Securing ABAP systems via iterated salted hash iSSHA-1. | SAP Blogs

Connect from AS ABAP to Google Cloud Platform App-Engine resource secured with Google Identity-Aware Proxy | SAP Blogs

CUA Log – Password hash is rejected; password is deactivated. Securing ABAP systems via iterated salted hash iSSHA-1. | SAP Blogs