![System Security Configuration Guide for Cisco NCS 540 Series Routers, IOS XR Release 7.3.x - Understanding MACsec Encryption [Cisco Network Convergence System 540 Series Routers] - Cisco System Security Configuration Guide for Cisco NCS 540 Series Routers, IOS XR Release 7.3.x - Understanding MACsec Encryption [Cisco Network Convergence System 540 Series Routers] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/300001-400000/360001-370000/364001-365000/364757.eps/_jcr_content/renditions/364757.jpg)
System Security Configuration Guide for Cisco NCS 540 Series Routers, IOS XR Release 7.3.x - Understanding MACsec Encryption [Cisco Network Convergence System 540 Series Routers] - Cisco
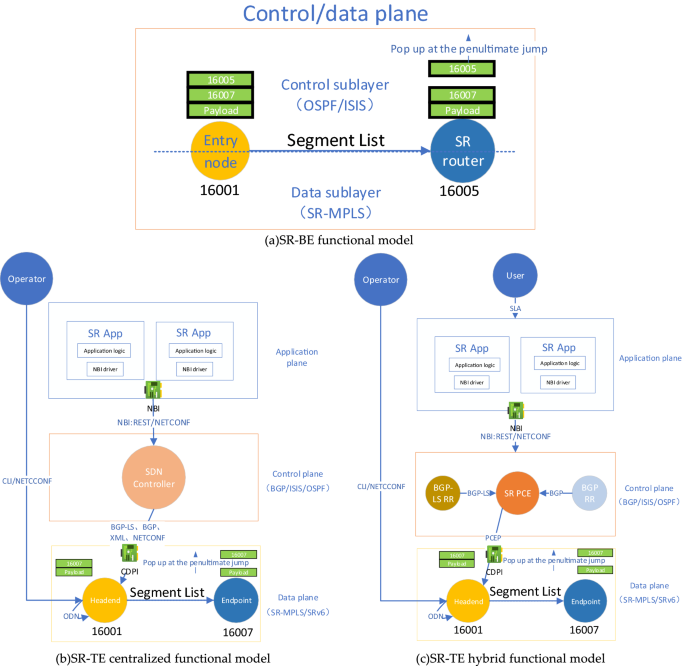
A data plane security model of segmented routing based on SDP trust enhancement architecture | Scientific Reports

Symmetry | Free Full-Text | Mitigation of Privacy Threats due to Encrypted Traffic Analysis through a Policy-Based Framework and MUD Profiles
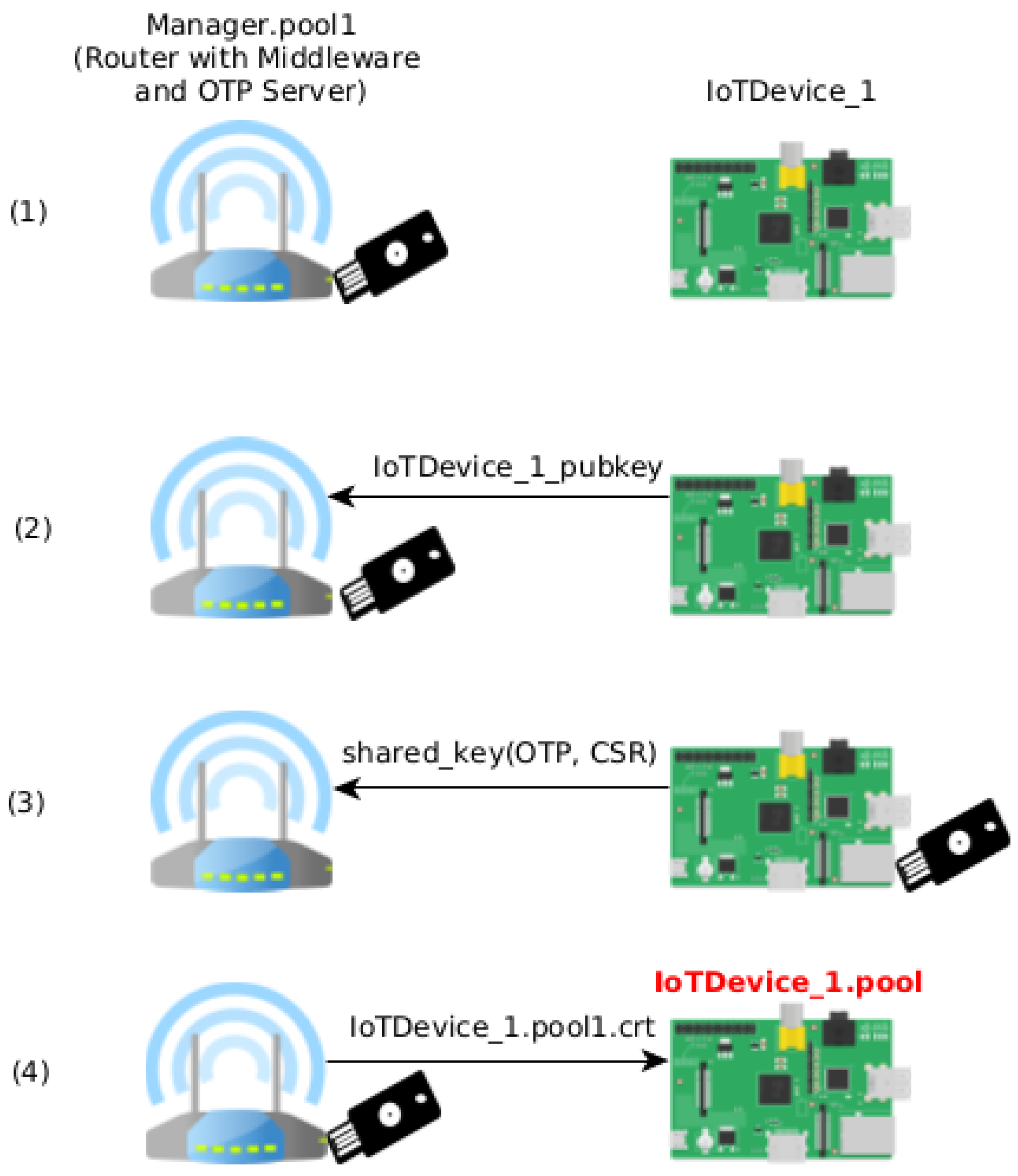
Sensors | Free Full-Text | Provisioning, Authentication and Secure Communications for IoT Devices on FIWARE
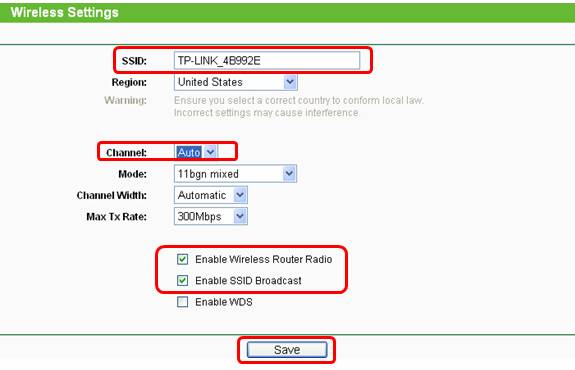
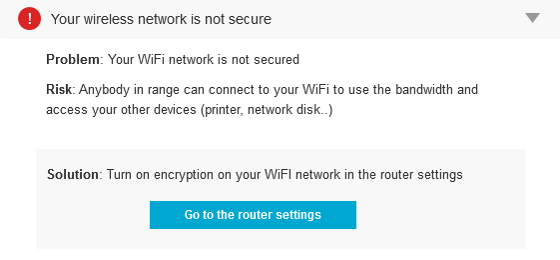
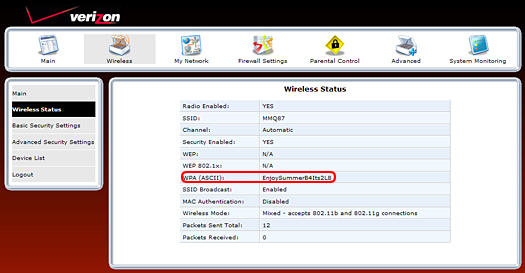
How do I secure/protect my wireless network by using WPA-PSK/WPA2-PSK on TP-Link Wireless 11N Router?
![Security Configuration Guide for vEdge Routers, Cisco SD-WAN Releases 19.1, 19.2, and 19.3 - Security Overview [Cisco SD-WAN] - Cisco Security Configuration Guide for vEdge Routers, Cisco SD-WAN Releases 19.1, 19.2, and 19.3 - Security Overview [Cisco SD-WAN] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/300001-400000/360001-370000/368001-369000/368448.jpg)
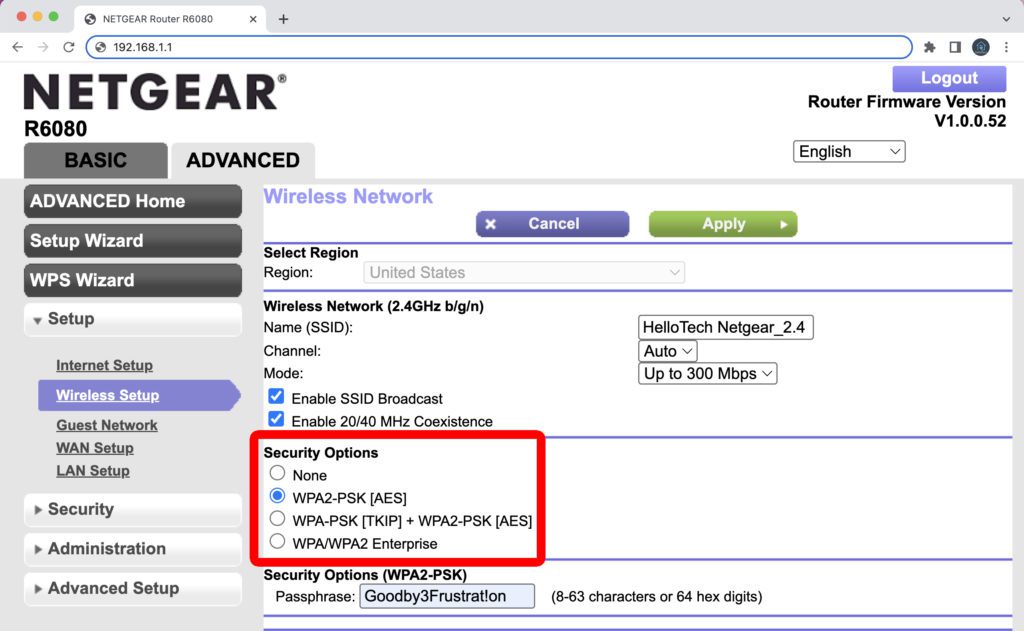
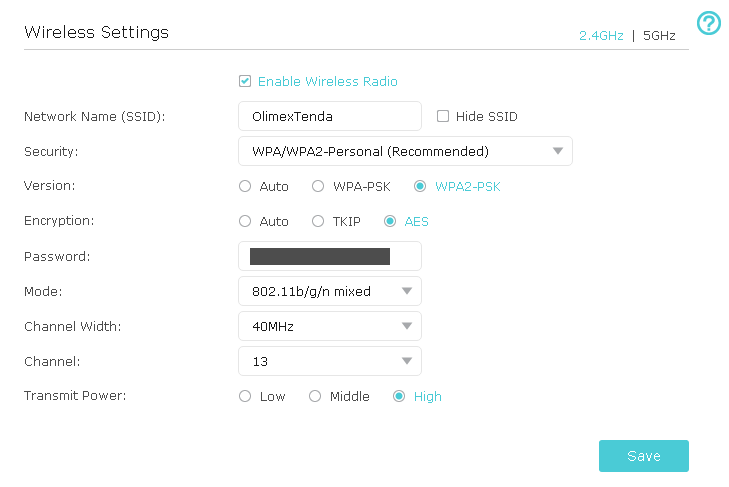
:max_bytes(150000):strip_icc()/comtrend-wireless-security-settings-5c47a3a646e0fb00019eb742.png)