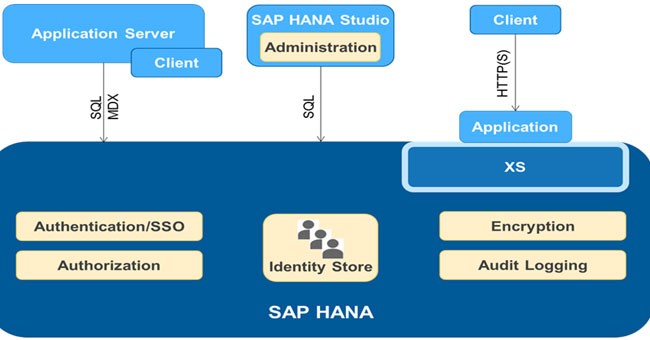
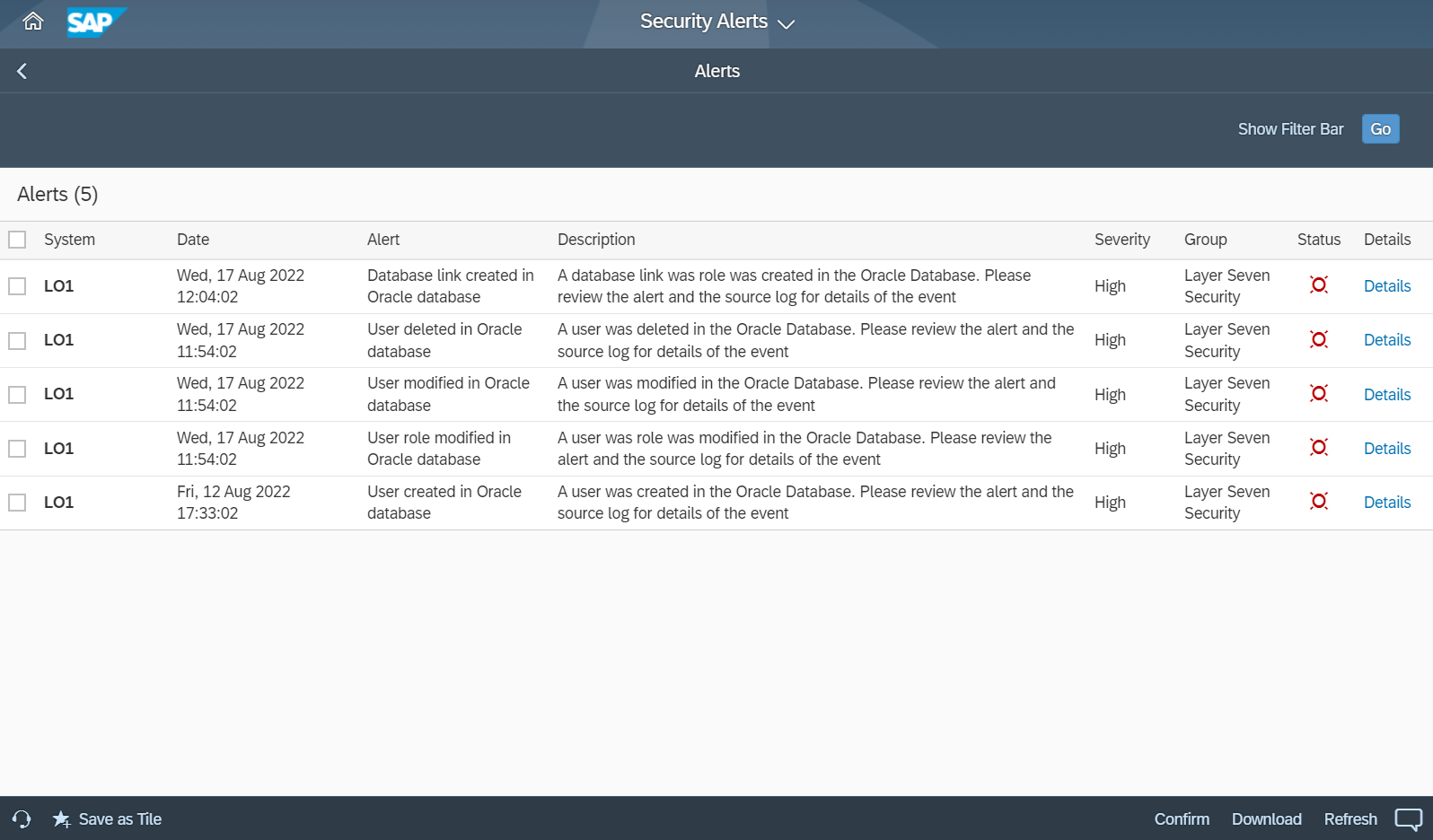
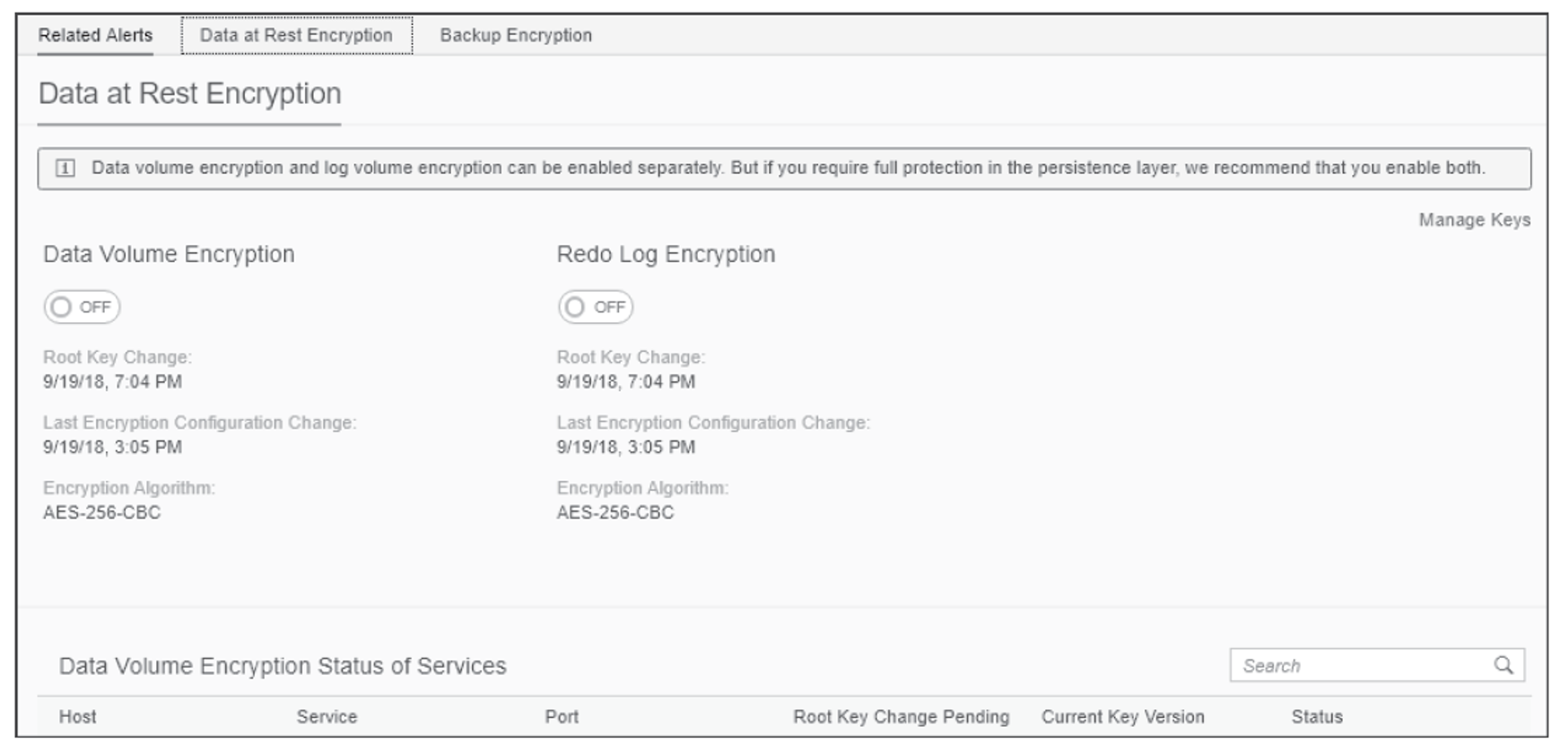
SAP HANA 2.0 Security Overview - SAP S/4HANA Training Tutorials for Beginners , S/4HANA , HANA Security , HANA BASIS Tutorial

HANA 2.0 System Replication - HA/DR - SAP S/4HANA Training Tutorials for Beginners , S/4HANA , HANA Security , HANA BASIS Tutorial

SUSE Linux Enterprise Server for SAP Applications 12 | Operating System Security Hardening Guide for SAP HANA for SUSE Linux Enterprise Server 12